Living off the Land (LotL) attacks involve the use of existing tools and tactics on targeted systems or networks to carry out a cyber attack. Why do attackers use LotL techniques? It’s simple. These techniques are easily accessible, capable of evading detection, highly adaptive, and supportive of automation. According to CrowdStrike’s 2022 Global Threat Report, 62% of attackers are using LotL tools or techniques in their attacks.
We at the Center for Internet Security (CIS) have published several guides to provide you with specific guidance on defending against many of these LotL techniques. These include PowerShell, Remote Desktop Protocol (RDP), Windows Management Instrumentation (WMI), and Server Message Block (SMB).The next guide in the series – Living off the Land: Scheduled Tasks – provides you with an overview of how this tool is legitimately used, how it is abused, and how you can use the CIS Critical Security Controls (CIS Controls) to protect against an attack that abuses scheduled tasks.
Attacks Abusing Scheduled Tasks
Part of defending against a LotL attack is knowing how the tool operates normally within your environment. This helps you understand what is normal and begins to establish a baseline in your systems for identifying when activity is abnormal.
Scheduled tasks are a common technique used by attackers to automate and perform malicious activities on target systems. In fact, Scheduled Task (T1053.005) was the seventh most prevalent LotL MITRE ATT&CK(R) sub-technique used in 2022, according to Red Canary. Attackers use scheduled tasks for a variety of reasons, including to initiate an infection, to recurrently establish persistence on a system, and to move laterally from system to system.
There are several ways an attacker can abuse scheduled tasks. Many of them are legitimate use cases, while others are more obvious in their malicious intent. Many threat actors abuse scheduled tasks and incorporate them into several malware variants. Some more well-known malware variants, past and current, that use scheduled tasks in their attacks include Tarrask (used by HAFNIUM), RedLine, Agent Tesla, Emotet, IcedID, Ryuk, TrickBot, and others.
Securing Scheduled Tasks
Unfortunately, a “block all scheduled tasks” approach to defense is not realistic. Your system administrators often use scheduled tasks to automate activities across the network so that tedious and time-consuming tasks are more manageable.
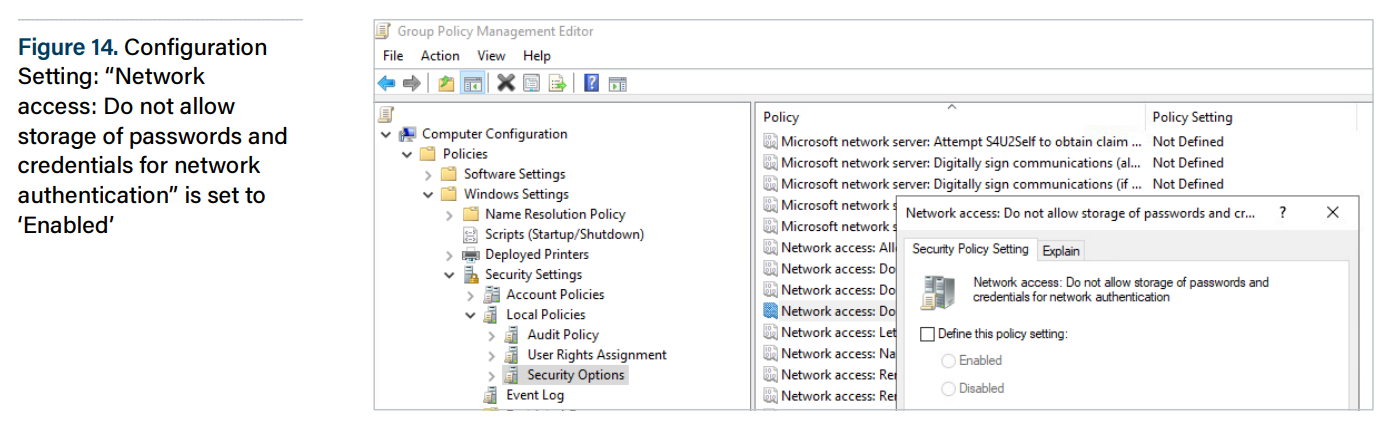
Living off the Land: Scheduled Tasks, page 11
Because of this, a defender’s approach involving LotL tools must be multi-faceted.
Ultimately, defending against a LotL attack does not need to be a reactive process. The CIS Controls offer a set of best practice recommendations that work together to develop a defense-in-depth approach to cybersecurity. Additionally, our CIS Benchmarks offer secure configuration guidelines for 100+ technologies, including operating systems, applications, and network devices. Combined, they form a formidable defense against a scheduled task attack.
With any good cybersecurity program, the first step in implementing defenses against any attack is to know your environment. In order to defend a network, you must first know what is on the network. This includes enterprise assets (e.g., workstations, servers), software, and data. Without taking this first step in your cybersecurity program, it is difficult to implement additional Safeguards. This includes Implementation Group 1 (IG1) Safeguards that are a part of CIS Controls 1, 2, and 3.
Once you’ve implemented these foundational Controls, there are several ways for you to proactively defend against an attack that abuses scheduled tasks. This guide provides six simple actions to help strengthen your defenses against a scheduled task attack. Please note that one size does not fit all, and you may need to adjust some settings based on the environment.
Strengthen Your Defenses Against LotL
Our guide breaks down each mitigation, explains the importance of securing Scheduled Tasks (from an attack perspective), and introduces related CIS Controls, CIS Benchmarks, and MITRE ATT&CK (sub-)techniques. By implementing the recommendations introduced in Living off the Land: Scheduled Tasks, you can confidently strengthen your cybersecurity posture while protecting your assets.
Valecia StocchettiSenior Cybersecurity Engineer

Valecia Stocchetti is a Senior Cybersecurity Engineer at the Center for Internet Security, Inc. (CIS(R)). As a member of the CIS Critical Security Controls team, she has led multiple projects, including the CIS Community Defense Model (CDM) v2.0, the CIS Risk Assessment Method (CIS RAM) v2.1, as well as multiple Living off the Land (LotL) guides. Most recently, Stocchetti was one of the principal authors of the Blueprint for Ransomware Defense.
Prior to joining the CIS Controls team, she led the Computer Incident Response Team (CIRT) at the Multi-State and Elections Infrastructure Information Sharing and Analysis Centers (MS-ISAC(R) and EI-ISAC(R)). While managing CIRT, Stocchetti spearheaded multiple forensic investigations and incident response engagements for the MS- and EI-ISAC’s State, Local, Tribal, and Territorial (SLTT) community.
Stocchetti came to CIS from the eCommerce field, where she worked complex financial fraud cases. She holds multiple certifications, including GIAC Certified Forensic Examiner (GCFE), GIAC Certified Forensic Analyst (GCFA), and GIAC Security Essentials Certification (GSEC). Stocchetti earned her Bachelor of Science degree in Digital Forensics from the University at Albany, State University of New York. She is currently pursuing a master’s degree in Information Security at Champlain College.
![]()
Post Disclaimer
The information provided in our posts or blogs are for educational and informative purposes only. We do not guarantee the accuracy, completeness or suitability of the information. We do not provide financial or investment advice. Readers should always seek professional advice before making any financial or investment decisions based on the information provided in our content. We will not be held responsible for any losses, damages or consequences that may arise from relying on the information provided in our content.



