The real-time cyber threat intelligence (CTI) Indicator Sharing Program from the Center for Internet Security (CIS) provides easy-to-implement indicator feeds available at no cost to U.S. State, Local, Tribal, and Territorial (SLTT) entities and election offices. Thanks to industry-standard formatting, the feeds are easy to ingest into most modern security and analysis tools and are integrated into other CIS service offerings. A key component of our vision for CTI, this program helps automate defensive actions, correlate events, conduct analysis, and make better, faster, more proactive defensive decisions.
The best threat intelligence doesn’t just identify potential threats. It helps predict and mitigate them. The CTI team combines specialized expertise in intelligence tradecraft and technical analysis with one of the largest data streams in the country to provide high value, actionable intelligence for our members. We help our members shift to predicting the next threat before it happens instead of waiting to identify when they’ve already become a victim.
Applications of the Feeds
Automated defensive actions, such as blocking associated traffic using firewalls and other perimeter devices, is one use of the feeds. Other members may wish to correlate activity in analytic environments or conduct their own analysis for incident response or threat hunting purposes.
In most cases, organizations don’t need any additional equipment to enroll in the Indicator Sharing Program. Examples of cybersecurity tools that can ingest our feeds include:
- Firewalls
- Intrusion Detection or Prevention Systems (IDS/IPS)
- Security Incident and Event Management (SIEM) platforms
- Security Orchestration and Automated Response (SOAR) tools
- Endpoint Detection and Response (EDR) agents
- Threat Intelligence Platforms (TIP)
- Trusted Automated eXchange of Intelligence Information (TAXII) platforms and other databases
Intelligence Sources and Indicators
We ingest threat data from more than 200 sources, including dozens unique to us and our federal partners, and we carefully distill it down to the highest impact indicators for our members. Intelligence sharing can be bi-directional with this service. While we’ll always share information with all of our members, any members who are able can also share intelligence with us to benefit the broader community.
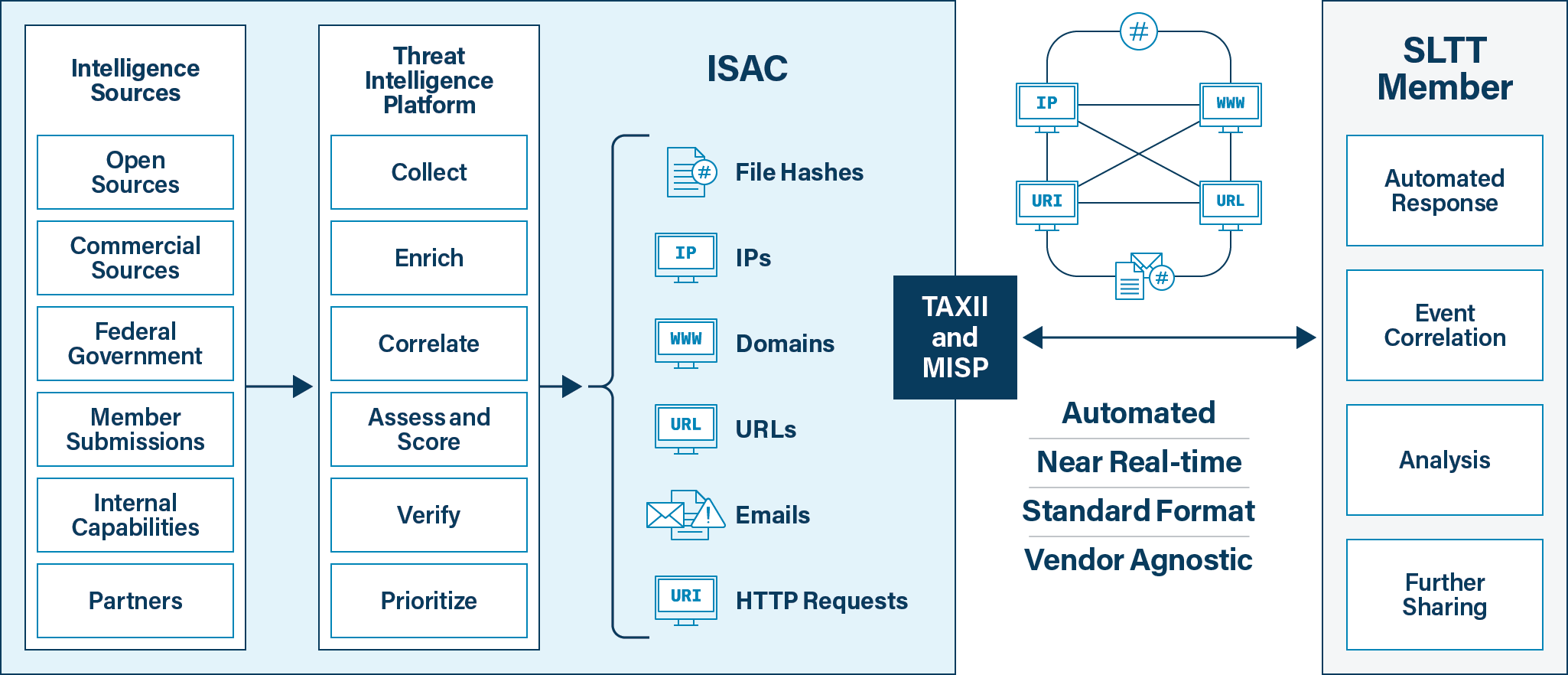 The MS- and EI-ISAC feeds contain the following types of indicators:
The MS- and EI-ISAC feeds contain the following types of indicators:
- Domains
- IPs (both v4 and v6)
- Full URLs (references to specific web resources)
- Email addresses
- File hashes
- Unique HTTP requests
As the data set grows and the feeds evolve, additional context surrounding these indicators will also be shared. This includes information such as registration information, relationships between indicators, associated threat groups, and more.
Standard Feed Formats
The feeds are available in standard formats to enable most members to ingest directly into their security devices.
Structured Threat Intelligence eXpression (STIX)
STIX is a free and open-source language and serialization format used to exchange CTI. CIS offers multiple collections that allow members to choose the kind of information that makes sense to ingest:
- MS-ISAC Collection – This collection contains indicators derived from MS-ISAC resources only.
- TLP: GREEN Collection – This collection contains only TLP: GREEN indicators
- TLP: WHITE Collection – This collection contains only TLP: CLEAR indicators
- Federal Collection – This collection contains indicators derived from the CISA Automated Indicator Sharing (AIS) community only.
- Curated Feeds Collection – This collection contains indicators derived from all sources available to the CIS CTI team.
Trusted Automated eXchange of Intelligence Information (TAXII)
TAXII is an application protocol specifically designed for transmitting STIX data. Members do not need to maintain their own TAXII infrastructure; local security devices only need to accept a STIX feed from our TAXII server.
Malware Information Sharing Platform (MISP)
MISP is a free and open-source software developed and maintained by the Computer Incident Response Center of Luxembourg (CIRCL). It’s designed to facilitate information sharing of threat intelligence, including but not limited to CTI.
The CIS MISP instance does not yet include all of the same information that is available in the STIX/TAXII feed, but we’re working on it! Stay tuned for more.
Get Started
U.S. SLTTs can get connected by emailing our team at [email protected].
To connect to the STIX/TAXII feed, you will be asked to provide the following information:
- Your contact information (individual or team) including primary contact name and email address
- Your SLTT organizational affiliation
- Public IP addresses or CIDR netblocks from which your organization will connect to the feed
- The subscribing device type (model and version)
- The STIX version(s) your device supports
If you are seeking to connect to our MISP collection, please specify upon contacting us as that is a separate process and different information will be required.
About the Author: The Cyber Threat Intelligence (CTI) team at the Multi-State and Elections Infrastructure Information Sharing and Analysis Centers (MS-ISAC and EI-ISAC) functions as the premier CTI source for all U.S. State, Local, Tribal, and Territorial (SLTT) entities and election offices. With decades of combined experience in all types of industries, the CTI team pushes out curated SLTT-centric threat intelligence reporting as well as malicious indicators via near real-time threat feeds. This information helps SLTTs anticipate and proactively defend against emerging cyber threats and shifts in adversarial tactics, techniques, and procedures. Additional information: team tradecraft and indicator feeds.
![]()
Post Disclaimer
The information provided in our posts or blogs are for educational and informative purposes only. We do not guarantee the accuracy, completeness or suitability of the information. We do not provide financial or investment advice. Readers should always seek professional advice before making any financial or investment decisions based on the information provided in our content. We will not be held responsible for any losses, damages or consequences that may arise from relying on the information provided in our content.