By Tony Sager, Senior Vice President and Chief Evangelist
In theprevious blog post, CIS’s CISO Sean Atkinson explained the value of aligning your cybersecurity roadmap to a robust framework like the CIS Community Defense Model (CDM) v2.0 and the CIS Critical Security Controls (CIS Controls) Navigator.
Now is the time where you’re ready to hit the road and put your cybersecurity roadmap into action. But you might have questions. Where do you start? How do you get the most out of this implementation phase?
In this blog post, I’ll identify a goal toward which your first step enacting your cybersecurity roadmap can lead. I’ll then discuss how you can build upon this progress to travel even further with your cybersecurity maturity.
Start with Essential Cyber Hygiene
By taking care with where you’re heading when you hit the road, you can lay a foundation of continual growth for your cybersecurity roadmap. It’s in this spirit that I recommend you start with cyber hygiene.
It’s easy to dismiss “cyber hygiene” as unimportant or less interesting. But without a specific definition, “cyber hygiene” is just a bumper sticker usually tossed out with some examples. (For example, “We all need better cyber hygiene managing administrative privilege.”)
At CIS, we’re one of the few to bring a specific definition and roadmap to this hygiene story through Implementation Groups. A definition becomes the basis for a plan along with a way to start measuring progress, communicate with management, and compare progress against others.
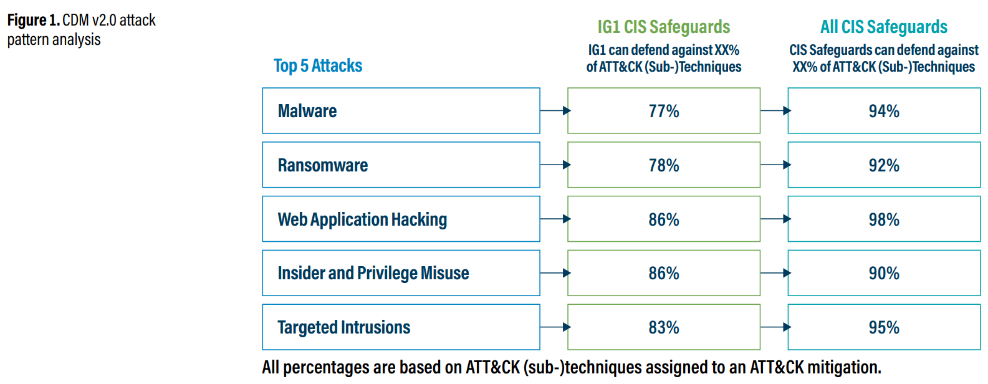
That’s why I recommend essential cyber hygiene, as embodied in Implementation Group 1 (IG1) of the CIS Controls. Our analysis is clear – there is tremendous security value in a set of foundational steps no matter how risky or complex your business situation. This is evident in CIS CDM v2.0. Indeed, by implementing IG1 Safeguards, you can defend against 77% of MITRE ATT&CK (sub-)techniques associated with today’s top attack varieties. These include malware, ransomware, web application hacking, insider and privilege misuse, as well as targeted intrusions.
Focus on Secure Configuration Management
As you make your way through IG1 of the CIS Controls, you’ll sooner or later find the need to manage your systems’ secure configurations. This isn’t unique to the CIS Controls. A fundamental security practice called out in every security framework (including the CIS Controls) is to manage the security configuration of IT components.
What is unique is the way CIS can help you harden your systems’ configuration. At CIS, we call these configuration guides CIS Benchmarks – and we are the world’s largest independent producer of this type of guidance. The CIS Benchmarks provide a vetted, trusted, industry-adopted basis for managing IT components. They don’t just provide consensus-driven recommendations for securing your systems. They also tell you the importance, the security benefit, and how you can prove that you’ve implemented each of those secure configurations.
What’s more, all CIS Benchmarks are mapped to the CIS Controls – including IG1 – at the recommendation level upon their release. This helps you harden your systems in accordance with essential cyber hygiene across your environments.

Automate Your Hardening Efforts
As we discussed in the previous section, CIS Benchmarks (either directly or through cloud images) are a tremendous starting point – industry-accepted with demonstrable security value. But they must also be actively managed, which establishes the need for a designed program of automation, reporting, and correction. That’s why automation, based on standards, has been a theme of the CIS Controls since their inception. A well-designed “machine” of IT and security automation is a key component of security reporting and compliance. It should produce most of the evidence and data needed to demonstrate the effectiveness of your security program or the security program of your customers to others (e.g., management, auditors, regulators).
In this spirit, we’ve designed CIS SecureSuite to provide Members with access to automation capabilities. Take the pro version of our Configuration Assessment Tool (CIS-CAT Pro), as an example. CIS-CAT Pro helps you run automated scans of your system’s settings against the security recommendations of the CIS Benchmarks, thus saving you time and money when taking a secure configuration policy and implementing it across your environment.
Such automation is especially useful if you’re a consultant or services provider working to help multiple clients strengthen their cybersecurity posture. It means you can help them with less manual effort on your part. In the process, you deepen the value of the services you bring to your clients.
Here’s some more information on how CIS-CAT Pro can help speed up your implementation of the CIS Controls.
Additionally, we’ve designed CIS SecureSuite to help Members with reporting and making corrections as necessary. Such is the case with the pro version of our Controls Self Assessment Tool (CIS CSAT Pro). It’s designed to help you track and prioritize your implementation of the CIS Controls v7.1 or v8. By identifying your current capabilities and gaps, you can use that information to evaluate which Safeguards they’ve implemented, assign tasks for new implementation tasks, and adjust accordingly as you make your way through the Implementation Groups of the CIS Controls.
The video below further discusses how you can improve your cyber defenses with CIS CSAT Pro.
You can use CIS CSAT Pro to strengthen your cybersecurity posture, but you can also leverage it to help your clients deepen their own cybersecurity maturity. To help organizations in the latter category, we created the CIS Controls-only SecureSuite Membership. Consultants and service providers can use this cost-effective, focused Membership to implement and measure against the CIS Controls for themselves and for their customers using CIS CSAT Pro, Controls content, and marketing assets.
Now through April 30, you can save up to 20% on a new CIS SecureSuite Membership using promo code CYBER2023. Check out our promo terms to learn more.
Gaining Ground Through Your Cybersecurity Roadmap
Enacting your cybersecurity roadmap is a journey. You can’t finish it all at once. By hitting the road and starting off with essential cyber hygiene through the CIS Controls, you can move on to manage your systems’ secure configurations via the CIS Benchmarks. From there, you can streamline your implementation of both using CIS-CAT Pro, CIS CSAT Pro, and other resources of a CIS SecureSuite Membership.
About the Author
Tony SagerSenior Vice President and Chief Evangelist

Tony Sager is a Senior VP & Chief Evangelist for the Center for Internet Security. He is involved in a wide variety of strategic, partnership, and outreach activities. He led the work which later became known as the CIS Critical Security Controls – an independent, volunteer-developed, cyber defense best practices program which is used throughout the industry. Tony has led numerous other activities to develop, share, scale, and sustain effective defensive cyber practices for worldwide adoption.
In addition to his duties for CIS, he is a volunteer in numerous cyber community service activities. He serves as an inaugural member of the DHS/CISA Cyber Safety Review Board, an advisor to the Minnesota Cyber Summit, and a member of advisory boards for several local schools and colleges. He is also a former member of the National Academy of Sciences Cyber Resilience Forum and serves on numerous national-level study groups and advisory panels.
Tony retired from the National Security Agency in 2012 after 34 years as a mathematician, computer scientist, and executive manager. As one of the Agency’s first Software Vulnerability Analysts, he helped create and lead two premier NSA cyber defense organizations (the System and Network Attack Center and the Vulnerability Analysis and Operations Group). In 2001, Sager led the release of NSA security guidance to the public and expanded NSA’s role in the development of open standards for security. Sager’s awards and commendations at NSA include the Presidential Rank Award at the Meritorious Level (twice) and the NSA Exceptional Civilian Service Award. The groups he led at NSA were recognized for mission excellence inside government and across industry with awards from numerous sources, including the SANS Institute, SC Magazine, and Government Executive Magazine.
![]()
Post Disclaimer
The information provided in our posts or blogs are for educational and informative purposes only. We do not guarantee the accuracy, completeness or suitability of the information. We do not provide financial or investment advice. Readers should always seek professional advice before making any financial or investment decisions based on the information provided in our content. We will not be held responsible for any losses, damages or consequences that may arise from relying on the information provided in our content.



