A new strain of malware developed by threat actors likely affiliated with the FIN7 cybercrime group has been put to use by the members of the now-defunct Conti ransomware gang, indicating collaboration between the two crews.
The malware, dubbed Domino, is primarily designed to facilitate follow-on exploitation on compromised systems, including delivering a lesser-known information stealer that has been advertised for sale on the dark web since December 2021.
“Former members of the TrickBot/Conti syndicate […] have been using Domino since at least late February 2023 to deliver either the Project Nemesis information stealer or more capable backdoors such as Cobalt Strike,” IBM Security X-Force security researcher Charlotte Hammond said in a report published last week.
FIN7, also called Carbanak and ITG14, is a prolific Russian-speaking cybercriminal syndicate that’s known to employ an array of custom malware to deploy additional malware and broaden its monetization methods.
Recent analyses by Google-owned Mandiant, SentinelOne, and PRODAFT have revealed the group’s role as a precursor for Maze and Ryuk ransomware attacks, not to mention exposing its connections to Black Basta, DarkSide, REvil, and LockBit families.
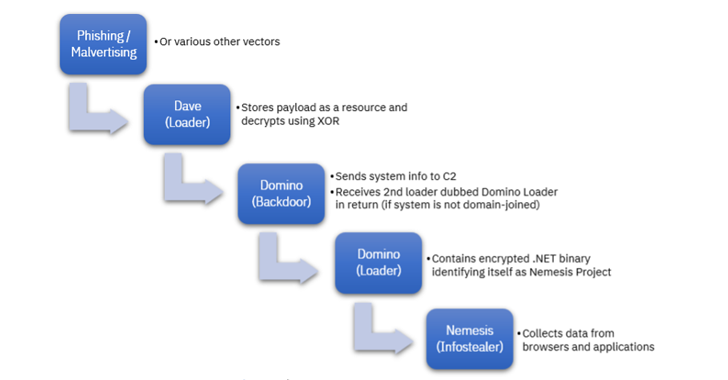
The latest intrusion wave, spotted by IBM Security X-Force two months ago, involves the use of Dave Loader, a crypter previously attributed to the Conti group (aka Gold Blackburn, ITG23, or Wizard Spider), to deploy the Domino backdoor.
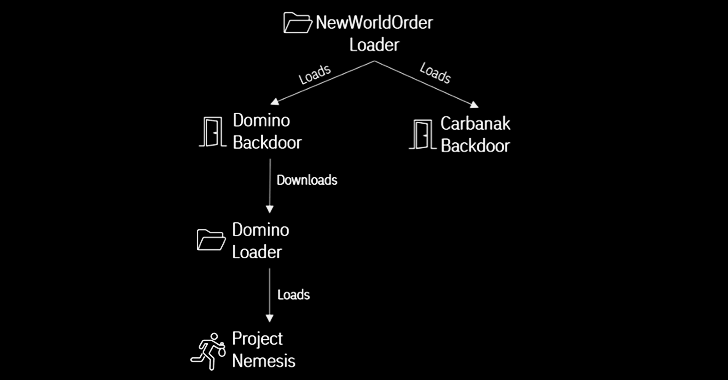
Domino’s potential connections to FIN7 comes from source code overlaps with DICELOADER (aka Lizar or Tirion), a time-tested malware family attributed to the group. The malware, for its part, is designed to gather basic sensitive information and retrieve encrypted payloads from a remote server.
This next-stage artifact is a second loader codenamed Domino Loader, which harbors an encrypted .NET information stealer referred to as Project Nemesis that’s capable of amassing sensitive data from clipboard, Discord, web browsers, crypto wallets, VPN services, and other apps.
“Domino has been active in the wild since at least October 2022, which notably is when Lizar observations began to decrease,” Hammond pointed out, indicating that the threat actors may be phasing out the latter.
Another crucial link bridging Domino to FIN7 comes from December 2022 that leveraged another loader called NewWorldOrder Loader to deliver both the Domino and Carbanak backdoors.
Master the Art of Dark Web Intelligence Gathering
Learn the art of extracting threat intelligence from the dark web – Join this expert-led webinar!
The Domino backdoor and loader – both 64-bit DLLs written in Visual C++ – are said to have been used to install Project Nemesis since at least October 2022, prior to its use by ex-Conti members earlier this year.
The use of stealer malware by ransomware distributors is not without precedent. In November 2022, Microsoft revealed intrusions mounted by a threat actor known as DEV-0569 that leveraged BATLOADER malware to deliver Vidar and Cobalt Strike, the latter of which eventually facilitated human-operated ransomware attacks distributing Royal ransomware.
This has raised the possibility that information stealers are deployed during lower priority infections (e.g., personal computers), while those belonging to an Active Directory domain are served with Cobalt Strike.
“The use of malware with ties to multiple groups in a single campaign — such as Dave Loader, Domino Backdoor and Project Nemesis Infostealer — highlights the complexity involved in tracking threat actors but also provides insight into how and with whom they operate,” Hammond concluded.
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.
Post Disclaimer
The information provided in our posts or blogs are for educational and informative purposes only. We do not guarantee the accuracy, completeness or suitability of the information. We do not provide financial or investment advice. Readers should always seek professional advice before making any financial or investment decisions based on the information provided in our content. We will not be held responsible for any losses, damages or consequences that may arise from relying on the information provided in our content.