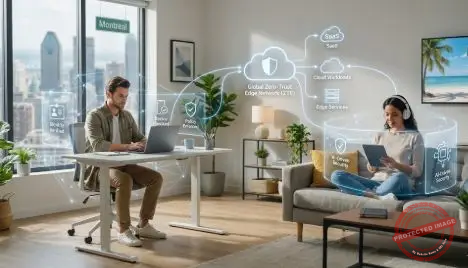
As remote work becomes the default rather than the exception, the traditional corporate perimeter has effectively disappeared. By 2026, Zero-Trust Edge security will be the de facto model for protecting remote and hybrid workers, bringing security controls as close as possible to users, devices, and applications.
The end of the corporate perimeter
The VPN-centric security model that dominated the first era of remote work is no longer sustainable. Traffic patterns are now wildly asymmetric: users connect from home networks, public Wi-Fi, and mobile devices to SaaS apps, cloud workloads, and edge services distributed across the globe.
Zero-trust principles—“never trust, always verify”—have emerged as the guiding philosophy for securing this environment. Zero-Trust Edge (ZTE) architectures apply these principles at the network edge, combining software-defined networking with cloud-delivered security services and granular identity-based access controls. Fortinet Check Point Software
Rather than tunneling all traffic back to a central data center, ZTE allows remote workers to connect directly to the apps and data they need, with dynamic policy enforcement and continuous authentication along the way.
Converging networking and security at the edge
In practice, Zero-Trust Edge converges several technologies: secure web gateways, cloud access security brokers, zero-trust network access (ZTNA), next-generation firewalls, and SD-WAN. Vendors and analysts increasingly view ZTE as an evolution of Secure Access Service Edge (SASE), with a stronger emphasis on zero-trust principles applied everywhere. paloaltonetworks.com
For remote teams, this means that security enforcement is no longer tied to physical locations. Policies follow the user and device regardless of where they connect from. A contractor working from a café in Montreal and a product manager working from a home office in Miami can both receive the same level of inspection, threat protection, and data-loss prevention as if they were on a corporate LAN.
As more workloads move to hybrid cloud and edge environments, ZTE nodes will also be deployed in colocation centers, telecom edges, and cloud regions, providing low-latency access while maintaining a consistent security posture.
Adaptive security for AI-driven remote workflows
By 2026, remote workflows will be dense with AI agents and copilots, many of which need broad access to enterprise data and applications. Zero-trust edge security will extend to machine identities, applying least-privilege principles to agents just as strictly as to human users.
Policy engines will evaluate not only user identity and device posture but also contextual attributes such as the specific agent requesting access, the sensitivity of the data, and recent behavioral patterns. Suspicious spikes in data access by an AI agent could trigger automated step-up authentication, throttling, or temporary access revocation until a human security analyst reviews the activity.
These capabilities rely on real-time telemetry and analytics drawn from across the ZTE fabric, where billions of daily transactions from remote workers provide rich signals about emerging threats and anomalous behavior.
Privacy, compliance, and user experience
One of the biggest concerns remote employees have about advanced security controls is privacy. ZTE solutions must strike a balance between inspecting traffic for threats and respecting personal boundaries, especially when workers use corporate devices on home networks that also support family members.
Modern architectures address this by segmenting traffic, inspecting only corporate flows while excluding personal applications or devices. They also provide transparent disclosures and opt-in controls where regulations require them. Compliance with evolving data protection frameworks in North America, Europe, and beyond will push ZTE vendors to offer more granular configuration of what is logged, how long data is retained, and who can access it.
From a user-experience perspective, the goal is to make Zero-Trust Edge invisible. Remote workers should notice stronger protection and fewer disruptions, not more friction. Intelligent routing, local edge points of presence, and optimized protocol handling help minimize latency so that secure access feels as fast as direct consumer-grade internet access.
Vendor landscape and strategic choices
Significant security and networking vendors now position Zero-Trust Edge platforms at the center of their remote work strategies. Industry evaluations highlight leaders based on their ability to deliver scalable cloud-native architectures, rich policy engines, and deep integrations with identity providers and endpoint tools. Zscaler
For enterprises, the strategic choice is not whether to adopt ZTE, but how. Some will move quickly to consolidate multiple point solutions into a single platform. Others will retain a multi-vendor approach, using interoperable APIs and standards to integrate best-of-breed components.
As remote-first organizations expand global hiring, ZTE will also be a key enabler of compliance with data residency and sovereignty requirements, ensuring that inspection and logging occur in the appropriate jurisdictions without compromising the overall security posture.
Closing thoughts and looking forward
By 2026, Zero-Trust Edge security will be the invisible guardrail enabling remote technologies to flourish. AI agents, XR collaboration platforms, and hybrid cloud applications all rely on a secure, resilient, and policy-driven network fabric. ZTE provides that fabric, turning the messy reality of “work from anywhere” into a manageable, auditable, and defensible architecture.
The organizations that thrive in this era will treat security not as a bolt-on but as a foundational design principle. They will invest in ZTE architectures that are cloud-native, identity-centric, and deeply integrated with their collaboration and productivity tools. In doing so, they will give remote workers the confidence to connect from anywhere, on any device, without compromising the safety of their data or their organization.
Co-Editors:
Dan Ray, Remote Technologies, Montreal, Quebec.
Peter Jonathan Wilcheck, Co-Editor, Miami, Florida.
References
What Is Zero Trust Edge (ZTE)? – Fortinet – https://www.fortinet.com/resources/cyberglossary/zero-trust-edge
What Is Zero Trust Edge (ZTE)? – Palo Alto Networks – https://www.paloaltonetworks.com/cyberpedia/zero-trust-edge
What Is Zero Trust Edge (ZTE)? – Check Point – https://www.checkpoint.com/cyber-hub/network-security/what-is-zero-trust-edge-zte/
SASE vs. ZTE: What Is the Difference? – Palo Alto Networks – https://www.paloaltonetworks.com/cyberpedia/sase-vs-zte
Zscaler Named a Leader in The Forrester Wave: Secure Access Service Edge Solutions, Q3 2025 – Zscaler – https://www.zscaler.com/blogs/company-news/zscaler-named-leader-forrester-wave-tm-secure-access-service-edge-solutions-q3
#RemoteTechnologies #ZeroTrust #ZeroTrustEdge #SASE #RemoteSecurity #HybridWork #IdentitySecurity #ZTNA #CloudSecurity #SecureRemoteAccess
Post Disclaimer
The information provided in our posts or blogs are for educational and informative purposes only. We do not guarantee the accuracy, completeness or suitability of the information. We do not provide financial or investment advice. Readers should always seek professional advice before making any financial or investment decisions based on the information provided in our content. We will not be held responsible for any losses, damages or consequences that may arise from relying on the information provided in our content.




 AMD
AMD TMC
TMC IE
IE MSI
MSI NOK
NOK DELL
DELL ECDH26.CME
ECDH26.CME